What is an API key?
API keys are used to identify and authorize the calling application or service. They are typically long-lived and static until rotated and often have a fixed set of permissions. They are primarily used for server-to-server communications or accessing public data, these tokens generally do not represent a specific user.
How do an API key work?
An API key is a long string of characters generated by the API provider and shared with authorized users. This key must be included in the request header when accessing the API. API keys are simple and effective for basic security needs. For example, popular services like Google Maps API and AWS provide API keys to control access and monitor usage.
curl -GET https://api.example.com/endpoint -H "Authorization: api-key YOUR_API_KEY"
API keys are not as effective as other forms of API authentication, such as OAuth and JWT, but they still play an important role in helping API producers monitor usage since it is the the most straightforward and widely used method to secure APIs.
What is its pros and cons?
Pros
- Simple to implement: API keys are easy to implement and use. They involve attaching a key to the request header, making it a straightforward method for developers and clients to understand and employ.
- Easy to monitor: API keys are easy to monitor. You can track the usage of each key and revoke them if necessary.
- Effective rate limiting: API keys are effective for rate limiting. You can set a limit on the number of requests per key to prevent abuse.
- Suitable for non-sensitive data: API keys are suitable for non-sensitive data or publicly available APIs, where security requirements are lower.
Cons
- Limited security: API keys are not secure enough for sensitive data, especially for client-side applications. They are often used in machine-to-machine communications.
- Not suitable for user Authentication: API keys are tied to applications or systems, not individual users, making it challenging to identify specific users or track their actions.
- No token expiry: API keys are typically static and don’t expire. If a key is compromised, it could be misused indefinitely unless manually regenerated.
What are the use cases for API keys?
- Service-to-service communication: API keys are suitable for scenarios where applications need to communicate with APIs directly through CLIs. E.g. Calling OpenAI APIs.
- Public APIs: When exposing APIs to the public, API keys provide a straightforward method of access control.
- Simplified setup: For quick and simple authentication needs, especially in development phase. Unlike Machine-to-machine authentication, API keys do not require client registration in prior, and do not need to exchange for an access token, either. You just pass your API key as a parameter in your request and it just simply works.
In real-world scenarios, the most common purpose when building products is product integration. Here is one typical use case:
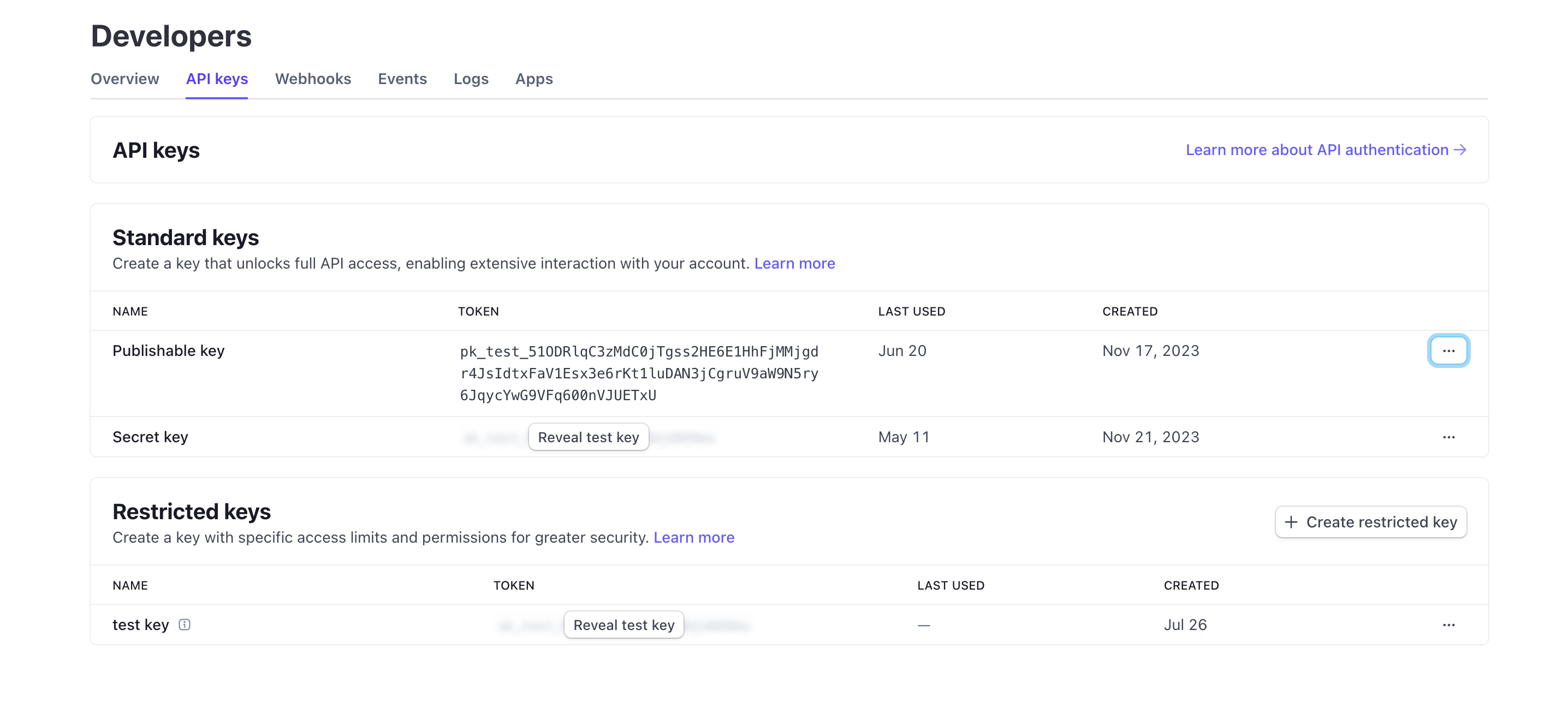
Example: Integration with Stripe
Stripe uses API keys for secure integration with different platforms and applications. You can create, view, delete, and manage these keys through the Developers Dashboard. By using API keys, you can integrate Stripe’s checkout and billing features into your product.
What is the difference between Personal Access Tokens (PAT) and Machine-to-Machine (M2M)?
When talking about API keys, personal access tokens and machine-to-machine can be also mentioned together since they all can programmatically access API resource through CLI commands, or establish communication between backend services.
Personal Access Tokens (PATs)
A personal access token is also a string but represents a specific user’s identity and permissions, is dynamically generated upon successful authentication or login, and typically has a limited lifespan but can be refreshed. It provides fine-grained access control to user-specific data and capabilities and are commonly used for CLI tools, scripts, or personal API access. The main difference is that it’s more specific and used for user-specific actions.
Machine-to-Machine (M2M)
M2M communication is when devices automatically exchange data without human involvement in a broader sense.
In the context of OIDC (or OAuth 2.0), M2M applications use the Client Credentials Flow, as defined in the OAuth 2.0 RFC 6749 protocol , which supports similar standard protocols. It usually involves a client application (a machine or service) accessing resources either on its own or on behalf of a user. It is ideal for situations where only trusted clients can access backend services.